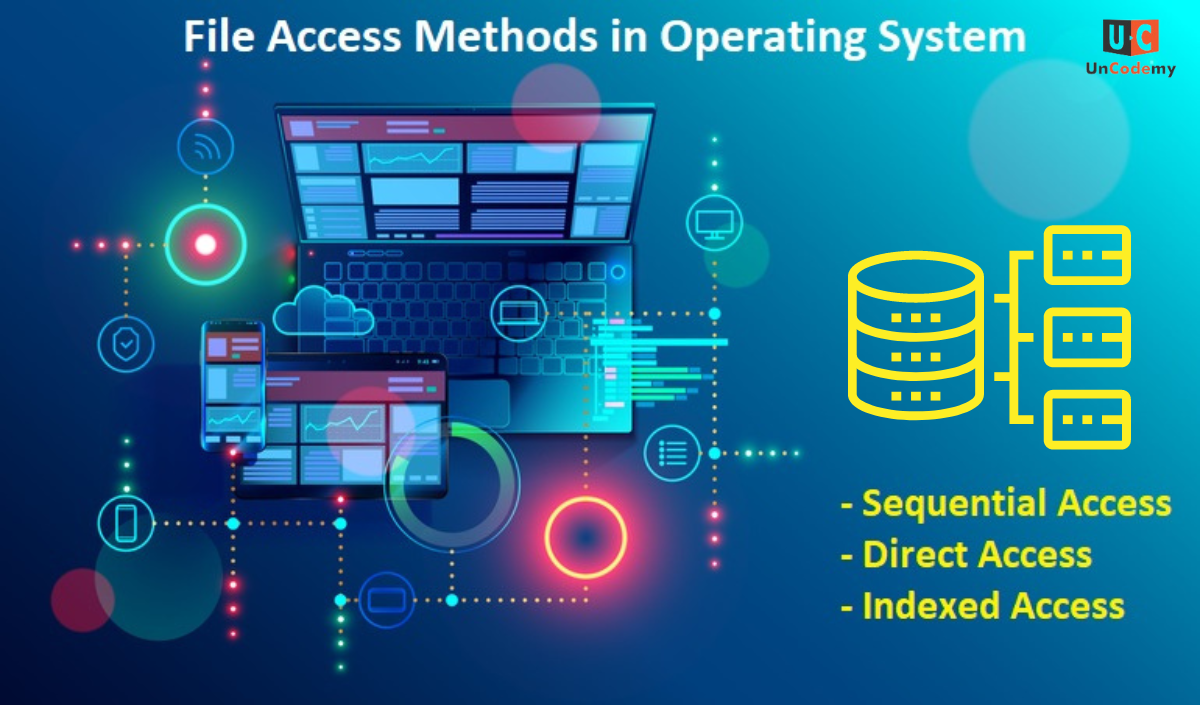
File Access Methods in Operating System.
The software or hardware of devices that communicate data between a computer and a distant device, such as a hard drive (or any other type of storage) or display station, is referred to as an access method (File Access Methods in OS) in computing. The phrase is occasionally used to describe the processes of placing or locating specific data in a specific location on a storage medium, followed by writing or reading the data. It is also used to describe how data is located within a dataset or file, two examples of larger data units.
The section of an operating system is in charge of formatting data sets and sending them to particular storage locations. Examples from the mainframe world include the Virtual Storage Access Method (VSAM) and Indexed Sequential Access Method (ISAM)
The process or program code used in local-area networks to arbitrate the use of the communications medium by providing access to specific stations only. Examples are Carrier Sense Multiple Access with Collision Detection (CSMA-CD) and token passing.
In the Sequential access system, you must pass through every point that overlaps to get from point A to point Z. You can skip right to the Z in the random access scheme. Tapes use Sequential access modes, whereas discs use random access modes.
When discussing data files, the terms “random access” and ” Sequential access” are frequently used. Anywhere in the random access data file is accessible for reading and writing. You can only read and write data in a serial access file sequentially, beginning at the beginning of the file.
advantages and downsides for both types of files. The Sequential access file is quicker if you always access the data in the same sequence. Random access is preferable if you have a tendency to access information that way.
File access methods in os:
The files have a lot of the data that the system needs. Execution may call for certain files that are stored in computer memory. We require extremely efficient methods for information retrieval that require the least amount of file access.
In this article, we will learn about the three types of file access methods. They are:
Sequential access method:
Editors and collectors frequently utilize it because it is among the simplest access techniques. Even if you used the same access method, you must have seen the soundbites. Records are organized into files. Records may be accessed by accessing the file. Each record is accessed sequentially and one at a time in the Sequential access method. For greater clarity, consider the photo below.
The majority of operating systems access the file in order. In other words, we can state that the operating system must access the majority of files in a particular order.
The operating system reads words from files during Sequential access. An indicator is preserved that initially relates to the file’s main heading. The indicator gives the user access to the file’s first word upon request and raises its value by the number 1. Up until the file’s conclusion, this process continues.
Modern word processing systems include the concepts of direct access and indexed access, but Sequential access—which requires sequential access to most files, including text, audio, and video files—is the way that is most frequently employed.
- very simple to carry out Similar to a linked list, work.
- Records are not a very efficient solution because they cannot be accessed at random.
- It moves slowly.
Direct access method:
Files are viewed as a collection of blocks or records when using the direct access approach, much as how a disc is viewed as being partitioned into blocks of equal size. This technique has the advantage of allowing random access to any block. The relative access method is another name for the direct access method. The operating system is the only one that knows the precise block address. The operating system uses the relative block number that the user provides when requesting access to a specific block to determine the exact block address.
In the case of database systems, the majority of direct access is necessary. Most of the time, we require data filtered from the database. Serial access may be inefficient and extremely slow in such circumstances.
If each storage block can hold 4 records, we know the record we require is in block X. Since it will need to pass through every block in order to get the relevant data, serial access won’t be used in this situation.
Despite the fact that the operating system needs carry out some sophisticated operations, including figuring out the needed mass number, direct access will produce the desired outcome. However, database programs typically implement this.
- Quicker compared to Sequential access.
- Access at random is permitted. Therefore, it’s not necessary to pass every obstacle.
- The application is simple.
Index sequential access/ index access:
The sequential access method’s fundamental flaw was that it forbade random access to file records or blocks. This issue is resolved by the index’s sequential access mechanism. This method uses an index that contains references to several file block indications. One must first access the index before being able to access any block in the file. From the index, we can then obtain indicators for various blocks.
An index can be created for a set of certain records if a file can be sorted in any of the fields. However, categorizing a specific record makes it accessible. The index is merely a file record address. Large databases can now be searched quickly and easily, but we needed more capacity to hold the catalog value.
As we had a cataloging block bearing hints to various additional disc blocks that were tailored for the file, this procedure is extremely similar to the customization of indexed files.
It is a modification to the sequential access technique. Access at random is permitted.
To track blocks, in addition, to file records, a separate catalog is required.
Due to memory constraints, the indicator might not be able to keep all indicators if the file size grows. A layered indicator could be utilized as a result.